TECHNOLOGY
Revolutionizing Meme Creation with Cursed-Memes.com Technology

Memes have become the universal language of the internet. From witty one-liners to exaggerated reactions, they have a unique power to unite, entertain, and even inform. Now, thanks to Cursed-Memes.com’s latest technological innovations, meme creation is entering an exciting new phase.
This blog will explore how Cursed-Memes.com is revolutionizing this form of digital expression through creative tools, automation, and a unique approach to meme curation. Whether you’re a casual meme lover or a dedicated creator, this innovation promises to make meme creation easier, more impactful, and—dare we say—more cursed.
The Evolution of Memes and the Challenge for Creators
Memes have come a long way since their earliest forms. However, creating high-quality, viral-worthy memes can still be time-consuming and labor-intensive. From finding the perfect image to crafting just the right caption, meme creators face several challenges, including:
- Time Constraints: Sourcing visuals and editing them with limited tools can take hours.
- Creativity Blocks: Coming up with original, humorous content is no small task.
- Accessibility: Advanced tools for meme creation are often expensive or lack user-friendliness.
Cursed-Memes.com aims to eliminate these barriers, democratizing meme creation through cutting-edge technology.
What Makes Cursed-Memes.com Technology Stand Out?
Cursed-Memes.com isn’t just another meme-generation site—it’s a platform built to significantly enhance the way memes are created and shared. Here’s how it achieves this transformation:
1. AI-Powered Meme Templates
One of Cursed-Memes.com’s most impressive features is its AI-powered meme template generation. Users no longer need to spend hours searching for the perfect stock images or recycling overused formats. The AI system identifies emerging trends and generates unique, contextually relevant meme templates that suit the creator’s desired tone—be it funny, dark, or absurd.
For example, if absurdist humor is your style, the system might suggest templates involving surreal animations or bizarre juxtapositions, perfectly optimized for modern “cursed meme” aesthetics.
2. Automated Captions and Suggestions
Stuck on what caption to write? Cursed-Memes.com steps in with its automated caption generator. Powered by vast meme databases and natural language processing (NLP), the tool suggests humorous or thought-provoking captions tailored to match the template. Creators can tweak the suggestions or add their personal flair before publishing.
Additionally, worded phrases like “Slightly cursed” or “Definitely cursed” classify themes, offering users an organized way to present their comedic intent. This not only saves time but encourages creativity by providing a baseline from which to build.
3. Real-Time Collaboration Features
Memes are often created collaboratively, whether it’s brainstorming ideas with friends or riffing off a trending topic. Recognizing this, Cursed-Memes.com incorporates real-time collaboration tools, allowing multiple users to work together on a meme. Think Google Docs, but for memes.
Creators can edit, comment, and vote on elements like images and text in one centralized workspace. This feature is particularly valuable for meme enthusiasts managing large social media accounts or communities.
4. Epic GIF and Video Reaction Library
Sometimes, a still image isn’t enough to convey the level of chaos and humor you’re aiming for. That’s where Cursed-Memes.com’s massive library of GIFs and short video clips shines. Designed for maximum comedic impact, these resources ensure users can create web content with visual variety and flare.
Best of all, these GIFs and videos are sourced or created with meme culture in mind—no need to sift through irrelevant or generic options.
5. Built-In Sharing Integration
What good is a meme if it isn’t shared? Cursed-Memes.com simplifies social sharing by offering direct integration with major platforms like Instagram, Twitter, TikTok, and more. You can instantly upload your meme, schedule posts, or even track engagement metrics, ensuring your content finds its perfect audience.
Why “Cursed Memes”? A Unique Approach to Humor
The “cursed meme” is more than just an internet trend—it’s a genre that captures the bizarre, unsettling, and often hilarious side of everyday life. By leaning into this style, Cursed-Memes.com offers tools that cater specifically to humor that’s absurd yet relatable.
From distorted images to strangely poetic captions, the platform helps creators push boundaries and explore new corners of meme culture.
How Creators and Brands Benefit from Cursed-Memes.com
This revolutionary platform isn’t just for individual meme enthusiasts. Its technology offers significant benefits for brands and social media marketers as well.
Increased Engagement
Memes are known for their ability to encourage reactions, shares, and comments. With the tools provided by Cursed-Memes.com, brands can easily create memes that resonate with their target audience—leading to increased visibility and engagement.
Cost and Time Savings
Rather than hiring designers or relying on expensive tools, businesses can use Cursed-Memes.com to quickly generate impactful visual content at a fraction of the cost.
Staying Culturally Relevant
Successful brand marketing often hinges on staying relevant and tapping into current trends. Cursed-Memes.com ensures you stay ahead of meme culture with its trend-predicting AI and dynamic template library.
Getting Started with Cursed-Memes.com
Getting started with Cursed-Memes.com is as easy as uploading your favorite image. Here’s a quick step-by-step guide to creating your first meme on the platform:
- Choose a Template: Browse the AI-suggested templates or upload your own visual.
- Customize Caption/Text: Use the caption generator for ideas or draft your own witty line.
- Enhance with GIFs or Animations (Optional): Add motion to your meme for more impact.
- Collaborate (Optional): Invite friends or team members to join in.
- Share with the World: Post your masterpiece instantly on your favorite social media platforms.
The platform is designed to make meme creation both fun and accessible, no matter your skill level.
Your Next Meme Revolution Starts Here
Meme culture is more powerful than ever, and Cursed-Memes.com is at the forefront of this digital evolution. With its advanced tools, collaborative features, and built-in sharing capabilities, the platform empowers creators and brands to express themselves like never before.
Whether you’re crafting memes for fun or using them to amplify your message, Cursed-Memes.com is your ultimate ally in the world of meme creation.
TECHNOLOGY
Data Migration as a Service: The Smarter Path to Cloud Transformation
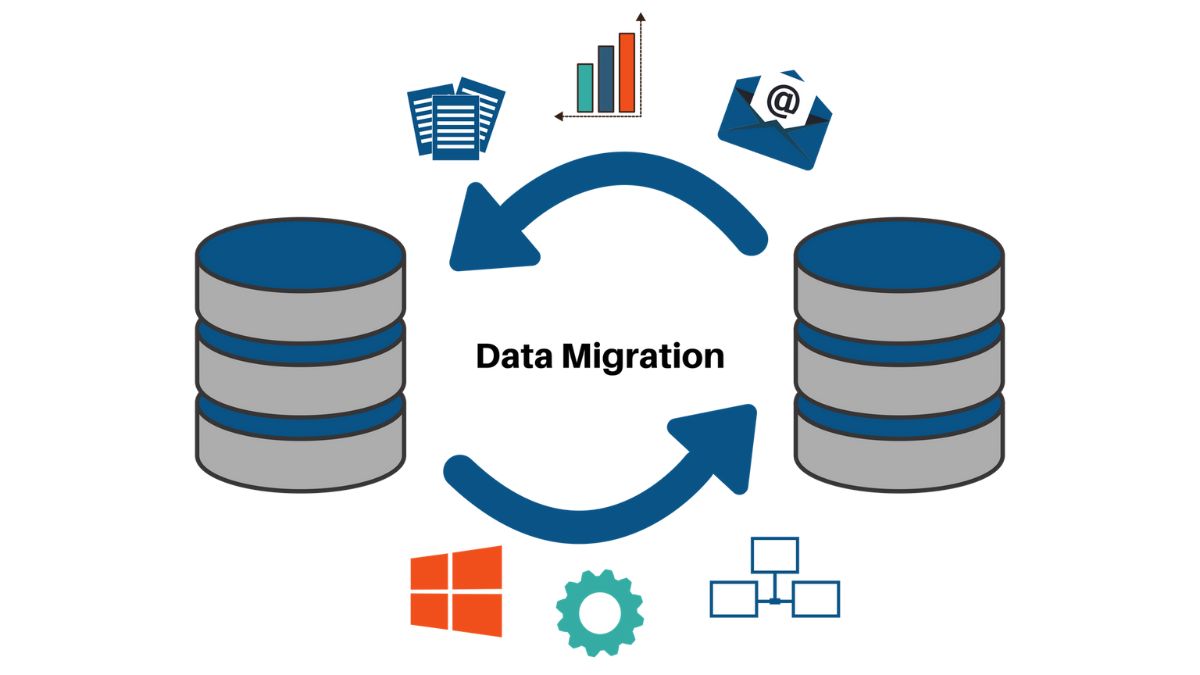
Every organization pursuing modernization faces the same critical challenge: moving data to the cloud. While often underestimated, this step ultimately determines whether digital transformation succeeds or stalls. Data migration is not simply about transferring files. It is about protecting data integrity, minimizing disruption, and establishing a reliable foundation for innovation.
To achieve this level of precision, enterprises are increasingly adopting managed, automation-led frameworks known as Data Migration as a Service. This structured approach combines governance, tooling, and specialized expertise to deliver clean, compliant, and future-ready cloud data environments.
Why Cloud Migration Is a Strategic Imperative
Cloud adoption has moved well beyond cost optimization. It is now a strategic requirement for competitiveness. Organizations rely on cloud platforms for scalability, security, and advanced analytics that traditional systems struggle to support.
Yet many transformation initiatives lose momentum when migration itself becomes a bottleneck. Fragmented data silos, legacy formats, regulatory constraints, and downtime risks can derail even the most carefully planned programs. Addressing these challenges requires a disciplined roadmap and expert execution, both of which are central to a service-based migration model supported by data migration consulting expertise.
Understanding the Modern Migration Model
Traditional migrations often rely on ad hoc processes led by internal IT teams juggling multiple priorities. This approach can lead to inconsistencies, untracked errors, and extended downtime. In contrast, a managed migration framework follows a repeatable, controlled methodology.
The process typically begins with data discovery and mapping, followed by cleansing, transfer, validation, and optimization. Each phase is automated and monitored to ensure accuracy at scale. Instead of manually moving data, enterprises leverage intelligent orchestration tools that track dependencies, flag anomalies, and maintain business continuity throughout the transition.
Benefits of a Managed Data Migration Framework
Data migration is both a technical and strategic initiative. When managed effectively, it does more than move information — it strengthens governance, improves visibility, and enhances the overall value of enterprise data.
1. Precision and Reliability
Automated validation and reconciliation ensure that data integrity is never compromised. These mechanisms detect discrepancies early and provide real-time feedback, reducing the risk of corruption or loss.
2. Speed and Operational Continuity
Predefined workflows and migration templates accelerate execution while minimizing downtime. Operations continue seamlessly, even as large volumes of data are transferred in the background.
3. Transparent Costs
By converting migration into a service, organizations gain clear visibility into cost structures. Predictable pricing replaces the uncertainty that comes with internally managed projects.
4. Built-In Security and Compliance
Encryption, access controls, and policy enforcement are embedded throughout. Providers align with ISO and GDPR standards, ensuring full compliance for regulated industries, including finance and healthcare.
5. Scalability for Growth
The framework scales effortlessly to accommodate evolving data volumes and hybrid architectures. Whether the target is Azure, AWS, or a private cloud, the same methodology applies across environments.
The Core Phases of a Successful Migration
A methodical approach transforms migration from a high-risk task into a controlled, measurable process. Each phase builds on the last to ensure consistency and confidence in the end result.
Assessment and Planning
A detailed assessment identifies data sources, dependencies, and business priorities. This insight guides timeline, resourcing, and sequencing decisions, ensuring alignment between IT strategy and operational needs.
Data Preparation and Mapping
Cleansing and standardization follow. Outdated, redundant, or incomplete records are removed. The remaining data is classified and mapped to the destination structure to ensure compatibility.
Execution
Automated tools transfer the data securely using encrypted pipelines. Progress is tracked through dashboards that provide transparency across business and IT stakeholders.
Validation
Post-migration checks verify completeness and accuracy. Reports reconcile migrated datasets with sources, confirming that every transaction and record remains intact.
Optimization
Finally, the new cloud environment is fine-tuned for performance and scalability. Indexing, storage tiering, and access controls are refined to ensure long-term efficiency.
Technology Enablers That Power Modern Migration
Modern migration strategies rely on automation, AI, and cloud-native orchestration. Platforms such as Azure Data Factory and AWS Glue streamline extraction and loading, while advanced analytics platforms supported through Databricks services enhance transformation, validation, and performance optimization at scale.
Machine learning further improves accuracy by identifying duplicates, predicting dependencies, and recommending corrective actions. Together, these capabilities reduce risk and significantly accelerate large-scale migration initiatives.
When a Service-Based Migration Model Makes Sense
A managed migration approach is particularly effective for organizations facing complex environments or major transformation initiatives, such as ERP modernization, mergers, or multi-cloud adoption.
It is well-suited when:
- Legacy systems lack direct integration with modern platforms
- Internal teams are constrained by capacity or expertise
- Regulatory requirements demand precision and uptime assurance
- The business needs to modernize rapidly without operational disruption
In these scenarios, a service-based model delivers accountability, resilience, and speed while allowing internal teams to focus on innovation rather than execution.
Migration as a Foundation for Continuous Innovation
Successful migration does more than relocate data. It fundamentally changes how data can be leveraged. Once centralized in the cloud, organizations can deploy advanced analytics, AI models, and automation to drive efficiency and insight.
A modern data foundation also simplifies future transitions. Subsequent migrations, expansions, or platform changes become faster and less disruptive when built on a standardized, service-driven framework.
Final Perspective
Cloud transformation begins with data, and the way that data is moved shapes everything that follows. Managed migration frameworks remove uncertainty, reduce risk, and provide a structured path toward scalable, secure modernization.
In an environment where agility defines competitiveness, adopting Data Migration as a Service is not merely a technical decision. It is a strategic investment in long-term resilience, innovation, and growth.
TECHNOLOGY
Atfboru: A Creative Platform for Designers, Artists, and Entrepreneurs

Unleashing Creativity with Purpose
Designers, artists, and entrepreneurs often find themselves at the intersection of creativity and business, where ideas converge and innovation thrives. Atfboru is a platform built to cater to this unique intersection—empowering professionals across industries to connect, create, and grow. Whether you’re a graphic designer showcasing your portfolio, an artist searching for collaborators, or an entrepreneur looking for tailored design solutions, Atfboru offers a space where inspiration meets opportunity. But what exactly makes this platform a go-to resource? This blog will explore the features, benefits, and opportunities Atfboru provides, and why it’s the perfect tool for anyone in creative industries.
What is Atfboru?
Atfboru (pronounced “at-for-you”) is a specialized platform designed to bring designers, artists, and entrepreneurs together. Unlike generic websites or job boards, Atfboru creates a supportive ecosystem where users can network, showcase their work, and build meaningful partnerships.
From hiring talented designers to finding rare art supplies, it’s a one-stop destination tailored to the creative community. With its diverse tools and features, Atfboru empowers users to make their mark in industries that thrive on originality and skill.
Features That Set Atfboru Apart
Atfboru is not just another platform—it’s a purpose-driven solution that makes life easier for creative professionals. Here’s what makes it unique:
A Hub for Portfolio Showcasing
For artists and designers, visibility is key to attracting clients or collaborators. Atfboru offers an optimized space to curate and display your portfolio online.
Responsive designs ensure your showcase looks immaculate on any device.
Portfolio analytics allow users to see who’s viewing their work and how they engage with it.
Customizable templates help reflect your unique brand and style.
Streamlined Client Collaboration
One of Atfboru’s standout features is its collaboration suite for freelancers and agencies. Here’s what you can expect:
Project management tools to organize deadlines, assets, and tasks.
Instant messaging for seamless client communication.
Document sharing and feedback integration so that ideas can flow without friction.
Marketplace for Creative Resources
Have you struggled to buy or sell niche design tools? This platform hosts a dedicated marketplace where users can find everything from exclusive art supplies to digital design templates.
Entrepreneurs can source logos, custom illustrations, or branding kits.
Artists and designers can sell stock images, limited-edition prints, or small-batch handmade goods.
Global Networking Opportunities
Community building is one of Atfboru’s core values. The platform connects you with peers, mentors, and collaborators worldwide.
Participate in global forums and discussions.
Join local meetups or virtual brainstorming sessions.
Access mentorship programs with top names in creative fields.
Educational and Business Tools
Success requires both talent and strategic know-how. Atfboru equips users with tools for strategic growth:
Workshops and webinars cover techniques, trends, and skill-building.
Business templates for contracts, invoices, and proposals simplify the professional side of creativity.
AI-powered recommendations suggest potential clients, collaborators, or projects aligned with your skills.
Why Entrepreneurs, Designers, and Artists Love Atfboru
Atfboru thrives because it’s built for creative individuals by those who understand the challenges of their professions. Here’s why the platform has gained such traction across creative industries.
For Entrepreneurs
Running a startup is demanding, and curating a memorable brand design takes significant effort. With Atfboru, entrepreneurs can easily hire vetted professionals, explore ready-made tools, and stay on track with strategic branding.
Example: Sarah, a bakery owner, collaborated with a graphic designer on Atfboru to create a logo that encapsulated her brand’s vision, leading to increased foot traffic and social media engagement.
For Designers
Beyond portfolio hosting, Atfboru is a dream come true for designers juggling freelance gigs, collaborations, and personal projects.
Example: A seasoned UX designer, Leo, found a mobile app project on Atfboru. Using the integrated project management tools, he delivered incredible results, earning a five-star rating and ongoing work with the client.
For Artists
The challenge for many artists lies in reaching the right buyers for their unique pieces. Through Atfboru’s marketplace and community, artists can showcase their talent and connect with an audience that values their craft.
Example: Maya, an illustrator, used Atfboru to sell limited-edition prints of her artwork, gaining both income and recognition.
How to Get Started on Atfboru
Joining Atfboru is as easy as 1-2-3:
Create Your Account: Sign up and fill out your profile to showcase your skills and specialties.
Explore Features: Set up your portfolio, upload content to the marketplace, or browse potential collaborators.
Engage with the Community: Join discussions, attend events, and post your work to attract the right opportunities.
Atfboru offers both free and premium plans, allowing you to scale your use of the platform based on your needs. With premium access, users unlock advanced insights, extended storage, and priority visibility.
Building the Future with Atfboru
Whether you’re designing, painting, or crafting a powerful brand, Atfboru offers the tools, network, and inspiration to take your creativity further. Partner with other like-minded individuals, and turn ideas into impactful projects that matter.
Creativity thrives in the right environment, and with Atfboru, you don’t just survive—you succeed. What are you waiting for? Your next big idea needs a platform.
TECHNOLOGY
7 Precision Solutions for Fleet and Equipment Repairs That Maximize Uptime

Meta Description: Discover proven precision repair solutions that keep your fleet running efficiently. Expert strategies to minimize downtime and reduce maintenance costs.
Fleet downtime costs businesses an average of $760 per vehicle per day, making precision repair solutions critical for operational success. Whether you manage a construction fleet, agricultural equipment, or commercial vehicles, implementing the right repair strategies can have a significant impact on your bottom line. This comprehensive guide explores seven precision solutions that will help you maintain peak equipment performance while minimizing costly interruptions to your operations.
1. Predictive Maintenance Through Advanced Diagnostics
Modern fleet management relies heavily on predictive maintenance technologies that identify potential issues before they become costly breakdowns. Advanced diagnostic systems use real-time data monitoring to track engine performance, hydraulic pressure, and component wear patterns. These systems can detect anomalies in engine temperature fluctuations, oil pressure variations, and unusual vibration patterns that often precede major failures.
Fleet managers who implement predictive maintenance programs report up to 25% reduction in maintenance costs and 70% fewer unexpected breakdowns. The key lies in establishing baseline performance metrics for each piece of equipment and setting automated alerts when parameters deviate from normal ranges. This proactive approach allows maintenance teams to schedule repairs during planned downtime rather than dealing with emergencies that can halt entire operations.
2. Specialized Component Rebuilding Services
Rather than replacing entire systems, precision rebuilding of critical components offers significant cost savings while maintaining reliability standards. Professional rebuilding services focus on restoring diesel engine components such as fuel injection systems, turbochargers, and cylinder heads to original manufacturer specifications. This approach extends equipment life while providing performance that matches or exceeds new part standards.
The rebuilding process involves comprehensive disassembly, precision machining, and reassembly using updated seals and wear components. Quality rebuilding services provide detailed documentation of work performed and often include warranties that rival new part guarantees. This solution proves particularly valuable for older equipment where new parts may be expensive or difficult to source.
3. Mobile Repair Units for On-Site Service
Deploying mobile repair capabilities directly to equipment locations eliminates the time and expense associated with transporting disabled machinery to service facilities. Mobile units equipped with diagnostic computers, precision tools, and common replacement parts can resolve approximately 80% of field breakdowns on-site. These units prove especially valuable for construction sites, agricultural operations, and remote industrial locations where equipment transportation presents logistical challenges.
Successful mobile repair programs maintain detailed inventory management systems that track parts usage patterns and ensure technicians carry appropriate components for their assigned equipment types. GPS tracking and dispatch software optimize response times, while digital work order systems provide real-time updates to fleet managers and equipment operators.
4. Precision Hydraulic System Maintenance
Hydraulic systems power critical functions in most heavy equipment, making their proper maintenance essential for reliable operation. Precision hydraulic maintenance involves regular fluid analysis, filter replacement schedules, and system pressure testing to identify developing problems. Contaminated hydraulic fluid accounts for approximately 75% of hydraulic system failures, making fluid cleanliness monitoring a crucial preventive measure.
Professional hydraulic maintenance includes comprehensive system flushing, seal replacement, and component calibration using manufacturer-specified procedures. Regular maintenance schedules should account for operating conditions, with more frequent service intervals for equipment operating in dusty or high-temperature environments. Proper hydraulic maintenance can extend component life by 300% compared to reactive repair approaches.
5. Computerized Parts Inventory Management
Effective parts management balances inventory investment with equipment availability requirements. Computerized inventory systems track parts usage patterns, lead times, and equipment criticality to optimize stock levels. These systems can automatically generate purchase orders when inventory reaches predetermined reorder points, ensuring critical components remain available without excessive capital investment.
Advanced inventory management incorporates equipment age, manufacturer recommendations, and historical failure data to predict future parts requirements. Integration with equipment monitoring systems provides automated alerts when specific components approach recommended replacement intervals, allowing maintenance teams to schedule work efficiently while parts are readily available.
6. Certified Technician Training Programs
Equipment complexity continues to increase, making ongoing technician education essential for precision repairs. Certified training programs ensure repair personnel understand proper diagnostic procedures, safety requirements, and manufacturer specifications. Technicians with current certifications complete repairs 40% faster with significantly lower callback rates compared to uncertified personnel.
Training programs should cover electronic diagnostic systems, hydraulic troubleshooting, and safety protocols specific to equipment types in your fleet. Regular skills assessments and continuing education requirements maintain technician competency levels while introducing new repair techniques and technologies. Investment in technician training typically generates returns of $3-5 for every dollar spent through improved efficiency and reduced rework.
7. Quality Control and Documentation Systems
Systematic quality control processes ensure repairs meet specified standards while providing accountability for work performed. Documentation systems track repair history, parts installed, and performance outcomes to identify recurring issues and optimize maintenance strategies. Digital work orders with photo documentation provide detailed records that support warranty claims and regulatory compliance requirements.
Quality control checkpoints should include pre-repair inspections, work verification procedures, and post-repair testing protocols. Regular audits of completed work help identify training needs and process improvements. Comprehensive documentation also supports equipment valuation for insurance and resale purposes while demonstrating maintenance compliance for regulatory inspections.
Implementing these precision repair solutions requires careful planning and investment in systems, training, and equipment. However, the resulting improvements in equipment reliability, reduced downtime, and lower total cost of ownership make these investments essential for maintaining a competitive fleet operation. Start by evaluating your current maintenance practices and identifying areas where precision solutions can deliver the greatest impact on your operational efficiency and profitability.
-

 NEWS3 months ago
NEWS3 months agoWhat is www.avstarnews.com and What Does It Offer?
-
 TECHNOLOGY7 months ago
TECHNOLOGY7 months agoGomyfinance Invest: Simplify Your Path to Financial Growth
-

 TECHNOLOGY3 months ago
TECHNOLOGY3 months agoAtfboru: A Creative Platform for Designers, Artists, and Entrepreneurs
-

 BUSINESS3 months ago
BUSINESS3 months ago.Ydesi: Exploring Its Significance and Applications
-

 CRYPTO6 months ago
CRYPTO6 months agoCrypto30x.com Gemini: Revolutionize Your Crypto Trading Experience
-

 NEWS1 year ago
NEWS1 year agoDogo News: The Latest Trends in the World of Dogo Argentino
-

 EDUCATION1 year ago
EDUCATION1 year agothe christian between the gospel and society
-

 ENTERTAINMENT1 year ago
ENTERTAINMENT1 year agoWWE SmackDown Episode 1491: Unforgettable Moments That Left Fans Roaring
